12 min read
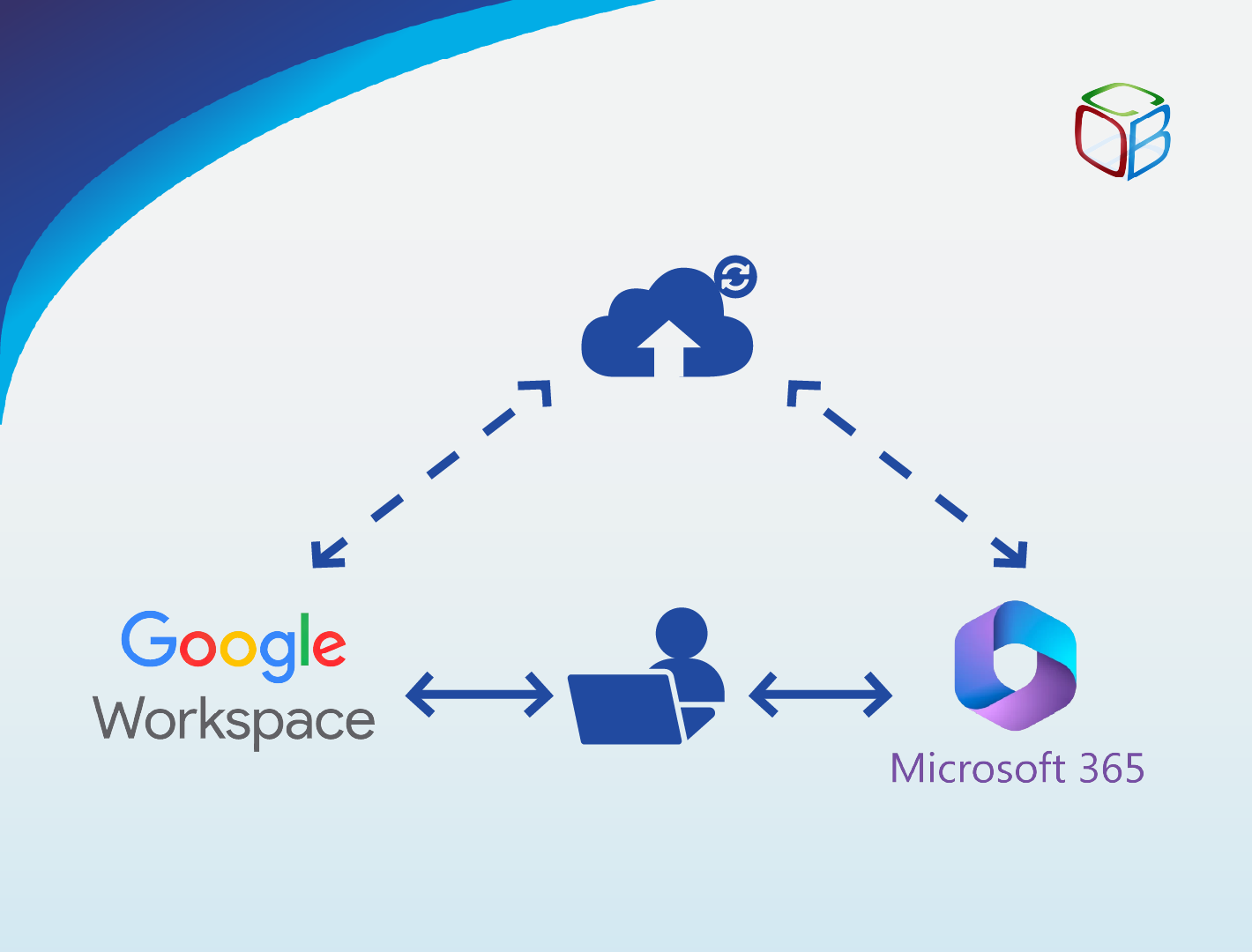
Is your business more suited for Microsoft 365 or Google Workspace?
Choosing the right cloud productivity suite is vital to shaping your company’s communication, collaboration, and workflow efficiency. Today, the top...
4 min read
 Kaitlin McDonnell
Aug 5, 2020 3:00:00 PM
Kaitlin McDonnell
Aug 5, 2020 3:00:00 PM

As technology advances, we are constantly exposed to additional avenues for it to permeate more deeply into our lives. The main driver is our own susceptibility to indulge in instant gratification and the time-saving powers of automation. And while automation gives us the power to do more with increasing efficiency and accuracy, it does come with a notable downside: the invasion of our personal privacy.
Many of us wouldn’t have a second thought about entering personal information into a website. We send emails, documents, pay bills, purchase goods — all online, and all using sensitive personal information to complete these transactions.
In 2019, when it was still normal to meet people face-to-face, I brought up the new (by legal standards) data protection law passed by the European Union, GDPR (General Data Protection Regulation). And, to my surprise, even many legal offices were unaware of this law passed in 2018 — especially because some of these firms managed estates for residents of the EU.
GDPR is a law that ensures all citizens of the EU have full control over their personal data online, and that their personal data is securely protected. After going into effect May of 2018, any business, no matter its revenue, size, or location that does business with any resident in the EU must abide by GDPR regulation.
Creating new privacy rights for EU citizens, GDPR enforces compliant data usage by imposing large monetary penalties for companies that misuse EU citizens’ personal data, or that are non-compliant with GDPR’s other standards. And “large” may qualify as an understatement — any business that is non-compliant with GDPR will face a 20 million Euro fine, or 4% of their annual revenue — whichever is higher.
GDPR may have been the first sweeping online privacy law, but it is by no means the last. In the United States, data privacy regulations are currently determined at the state level. Going into effect in January 2020, California passed the CCPA, otherwise known as the California Consumer Privacy Act. Other states are following suit: New York, Maryland, Massachusetts, Hawaii, and North Dakota are all actively developing and amending their own data privacy legislation.
Data protection laws, while all slightly different, operate in much the same way: they create rights for an individual to access, correct, delete, or opt out of sale and personal information. Failure to comply with these regulations often results in heavy fines (as in the case of GDPR).
Due to these new regulations, organizations must consider how they collect, store, and process personal information. Personal information includes:
To avoid any penalty, you will want to make sure your organization has processes in place to ensure personal information is protected from the moment it is created to the time it is deleted.
Data protection laws are not limited to online data either — all forms of communication with customers, whether electronically or on paper, must have consent for their inclusion on any particular marketing campaign. As a result, it is in your best interest to include privacy statements and disclosures for clients to review and sign before allowing them to give any personal information to your business.
With every communication sent to a customer, proof of that customer’s consent must be provided, in the event that an individual objects to receiving communication from your business. It is always best practice to carefully audit any customer data your business holds, and make sure all data is time stamped with reporting of what data and communications a contact opted into, and how they opted into it.
In order to protect your business, it is important to restrict who within your organization can access customer information. Identify where sensitive customer data resides in your organization, who can access it, and if there are any risks associated with that data.
Also, take into consideration what would happen should there be a data breach or suspicious activity on your organization’s network. Develop safeguards throughout your infrastructure to contain any data breaches — make sure to constantly update and maintain your cybersecurity, and have processes in place to take quick action to notify individuals and the authorities if a breach does indeed occur.
This advice even applies to any vendors your organization works with — if a vendor interacts with your client data, and they misuse that data, your business is responsible.
First things first — analyze what data is necessary, and what is not. We often collect data that is superfluous simply because we can — but why? Take a hard look at the data you collect, and ask yourself, and others in your organization the following questions:
A major blind spot when business plan for data protection compliance is their multi-function printer or copier. Because these devices are connected to your business’ network, they are tempting targets for hackers to use to steal sensitive data from the machine’s hard drive.
Employees are also likely to leave documents sitting in output trays, allowing anyone to steal the personal information residing on these documents. Luckily, there are a number of copier manufacturers that provide security features that help to prevent these risks from occurring.
In order to leverage these security features, you don’t always need the newest device on the market. Reach out to your business improvement specialist to ask if there are ways to better protect your organization, starting with your devices. They will be able to provide insight into creating a more secure and compliant environment.
These considerations are even more important due to the enforce remote work situations many employees face because of COVID-19. There are a few questions to ask yourself if your organization is currently remote:
Now, more than ever, is the time for organizations with IT departments to work closely with employees to understand how they are handling data, and how they can work to make it more secure, while simultaneously streamlining workflows.
So many companies look at integrating new software as a mundane task that is avoided until it is needed, or as something to be feared due to the fallout of organizational change. But now is the time to incorporate these new solutions and processes. Now is the time to make that investment for prevention, rather than a response to an already existing issue.
12 min read
Choosing the right cloud productivity suite is vital to shaping your company’s communication, collaboration, and workflow efficiency. Today, the top...

3 min read
Cobb Technologies has been honored as one of the 2025 Best Places to Work in Virginia by Virginia Business and Best Companies Group. This prestigious...

5 min read
Cobb Technologies is honored to hold the SWaM (Small, Women-owned, and Minority-owned Business) certification, awarded by the Commonwealth of...